On Demand Assessments
Security Controls Validation
Simulate real attacks and use AI-driven insights to prioritize and reduce your threat exposure.
Our Security Controls Validation service is designed to test an organization’s security posture by simulating various stages of a cyberattack, from initial compromise to data exfiltration. The primary goal is to simulate the tactics, techniques, and procedures (TTPs) of real-world cyber attackers to validate the effectiveness of your endpoint prevention and detection mechanisms against emerging threats.
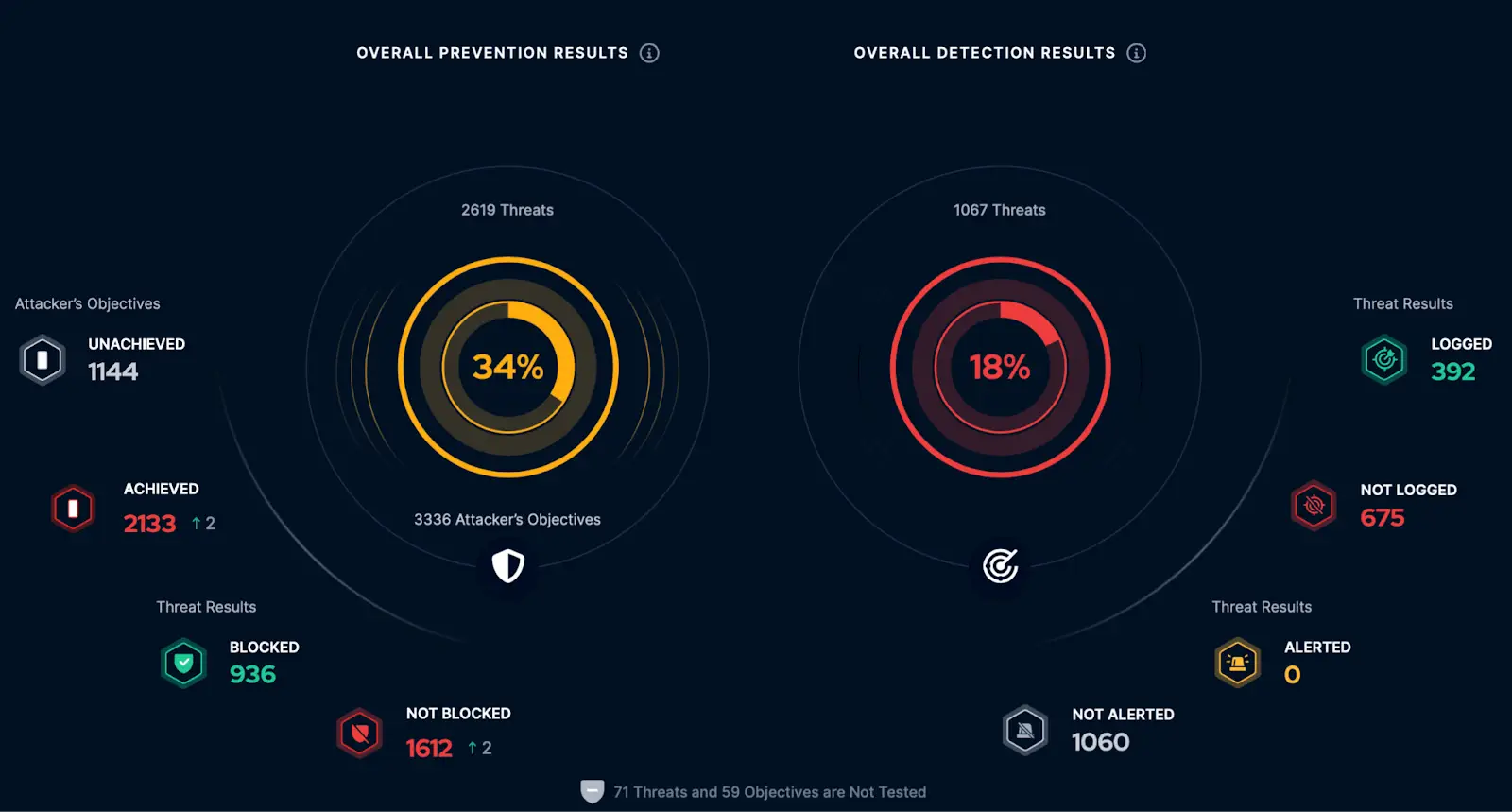
BAS (Breach and Attack Simulation) validates an organization's security posture by testing its ability to detect a portfolio of simulated attacks performed by SaaS platforms, software agents, and virtual machines. In addition, it generates detailed reports about security gaps and prioritizes remediation efforts based on the risk level. The typical users of these technologies are financial institutions, insurance companies, and more "
GARTNER
Use Cases
Our Managed Breach and Attack Simulation service is designed to test an organization’s security posture by simulating various stages of a cyberattack, from initial compromise to data exfiltration. The primary goal is to simulate the tactics, techniques, and procedures (TTPs) of real-world cyber attackers to validate the effectiveness of your endpoint prevention and detection mechanisms against emerging threats.
Validate Endpoint Security Controls
Validate against advanced threats including emerging threats and ransomware.
Ransomware Readiness
Validate and enhance your ability to defend against the latest ransomware threats, closing security gaps swiftly.
Security Posture Validation
Assess and quantify the effectiveness of security your controls to prevent, detect and respond to attacks across the cyber kill chain.
Cloud Posture Validation
Identify common cloud misconfigurations and overly permissive IAM policies - the two primary causes of cloud data breaches.
OVERVIEW
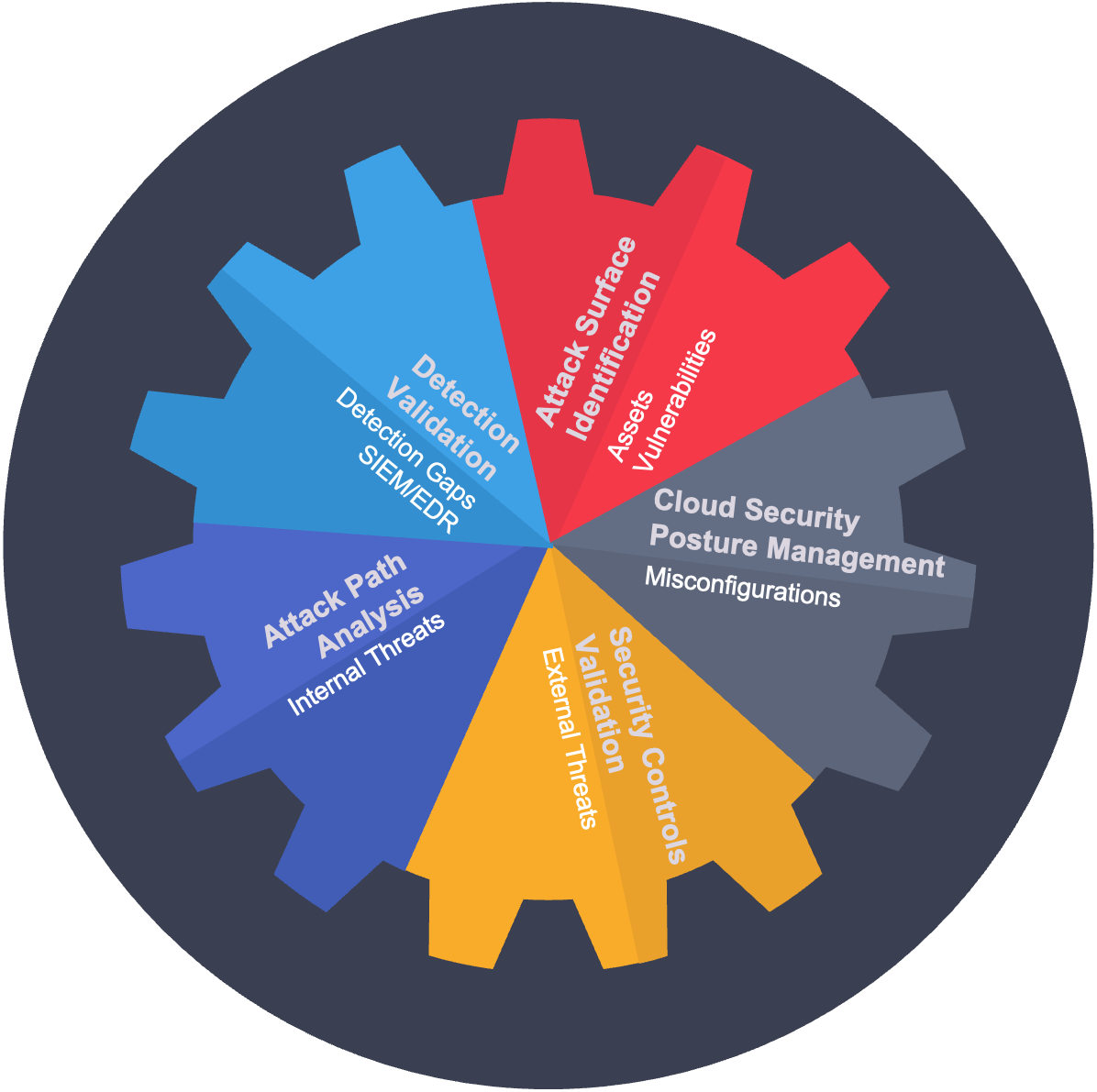
Customized simulations for better adversary insight
Have your security controls been tested? Do you know if they are ready to respond effectively to today’s attack patterns? Satius Security Breach & Attack Simulation platform combines the expertise, best tools, and the MITRE ATT&CK framework to perform customized simulations to your environment.
With deep knowledge of the industry, market and geographical factors which influence the threat landscape, we craft a series of highly trackable and repeatable breach simulations to prepare your systems and teams for likely threats. Combined with any specific requirements your organization may have, we will layer industry standards and years of experience to help test your ability to detect and respond to indicators throughout the kill chain. We will then support your organization in identifying and prioritizing next steps for your security team.
- Measure and optimize the protection provided by existing security controls
- Discover and eliminate attack paths to critical systems and users
- Optimize detection and response capabilities to eliminate attacks sooner
How Satius offers BAS services

BENEFITS
How the Satius Managed Breach and Attack Simulation strengthens your security posture
Accelerates mitigation of security gaps
Get the insights you need to not only proactively identify security gaps but also address them before they are exploited by adversaries.
Supplies a holistic and continuous view
Understand at any moment your organization’s readiness to defend against the latest threats by validating security effectiveness in key areas.
Evidences threat readiness and ROI
Obtain the metrics and insights you need to make data-driven decisions, be threat-centric, and demonstrate assurance and value to business leaders and auditors.
Automates manual validation processes
Address security risks sooner by automating manual assessment processes and by empowering your team to focus on remediation rather than discovery.
KEY FEATURES
Why your organization needs BAS
- Making significant changes to infrastructure
- Launching new products and services
- Undergoing a business merger or acquisition
- Preparing for compliance with security standards
- Bidding for large commercial contracts
- Utilising and/or developing custom applications
CAPABILITIES
What Types of Attacks Can Be Simulated?
Satius Breach and Attack Simulation (BAS) service can simulate a wide range of attack scenarios, covering various tactics, techniques, and procedures (TTPs) employed by cybercriminals. Depending on the client’s need for on-demand assessment or the continuous managed service, some common types of attacks that can be simulated with BAS include:
Test the effectiveness of your Email Security solutions against both malicious attachments and malicious URLs. Email attacks can be simulated quickly without the need of installing a further agent and works with all kinds of email solutions, such as M365, Google, etc.
BAS can accurately simulate the behavior of various malware and ransomware infections, including downloader or wiper malware, stealthy infostealers or backdoors to test the effectiveness of endpoint protection solutions, threat detection mechanisms, and incident response capabilities. By simulating real-world attacks, BAS allows organizations to evaluate their ability to prevent, detect, and remediate malware infections, even as these threats continue to evolve.
This assessment focuses on automated behavioral detection (EDR), signature-based detection (anti-virus), known vulnerabilities and patches on various tools including Windows and 3rd-party software, hardening of your endpoints, Ransomware, etc.
software, hardening of your endpoints, Ransomware, etc.
Simulate Data Exfiltration of sensitive data over typical covert channels, leveraging various protocols, ports, and file formats. The platform supports many critical data types such as Personal Identifiable Information (PII), payment card data, source code, etc.
Expose your security infrastructure to Lateral Movement attacks and get insight into the extent of the outreach and the potential impact.
BAS can simulate sophisticated credential-based attacks that leverage advanced access methods, such as Local Security Authority Subsystem Service (LSASS) dumping and Local Security Authority (LSA) secrets extraction. These techniques allow attackers to obtain sensitive authentication data, bypassing typical security controls that may quickly detect and raise alerts for more common methods like brute force or spray and pray attacks. By simulating these advanced access methods, BAS platforms help organizations identify potential weaknesses in their credential protection mechanisms and enhance the security of their authentication processes.
Simulate multi-stage attacks used by APT groups, such as APT42, Gamaredon, MuddyWater, and Cozy Bear (APT29), to test an organization’s ability to detect, respond to, and recover from highly targeted and sophisticated threats. APT groups often employ advanced tactics, techniques, and procedures (TTPs), including custom malware, exploitation of unpatched and critical vulnerabilities, and lateral movement techniques, to infiltrate their targets and maintain a persistent presence.
Our security qualifications
Our experts hold numerous industry certifications and vendor specific certified trainings to insure standardized approach and optimal results.
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.
TESTIMONIALS
What our clients say about us

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial






