On Demand Assessments
Dynamic Application Security Testing
Unlock security testing, vulnerability management, and tailored expertise.
Organizations are faced with rapidly expanding application portfolios, both in size and complexity. Securing applications from risk and vulnerabilities has become a business imperative to protect the business and protect customers.
Satius Security’s On-Demand Dynamic Application Testing offers a cost effective
OVERVIEW
Protect Applications throughout the Software Development Lifecycle
Applications must be protected across all phases of the Software Development Lifecycle (SDLC) to make a Software Security Assurance program successful. Application security begins when code is developed. Code is validated through testing and is continuously monitored once the application moves into production. Application security programs embedded throughout the SDLC have been proven to be the most cost-effective way to ensure policy execution, compliance, and on-going enforcement.
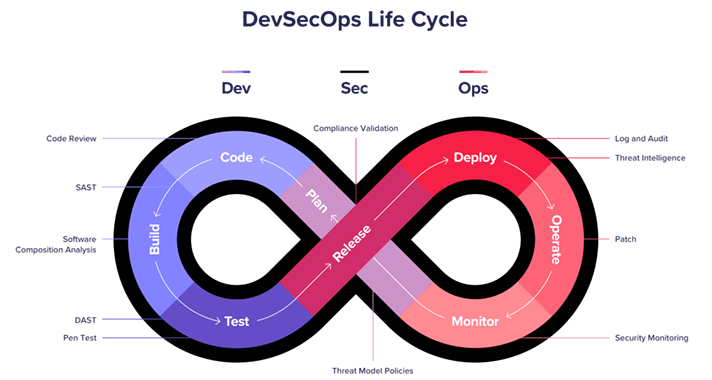
Dynamic assessments complement Static Application Security Testing of source code because they identify vulnerabilities that can be detected only in a live/simulated production environment. Examples of vulnerabilities detected only through dynamic testing range from configuration related vulnerabilities to sophisticated hacking techniques and specific attack vectors against an application’s business logic.
Value On Demand
Our DAST technologies support web applications, web services, and mobile-browser optimized applications. What makes Satius on Demand DAST assessments unique is that they integrate three essential components: WebInspect automated testing, manual analysis, and optional active IAST.
Realistic
Mimic real-world hacking techniques and attacks on targeted applications
Coverage
Provide comprehensive security analysis of complex web applications and web services
Comprehensive
Crawl the entire attack surface to find exploitable vulnerabilities
Remote
Can test internal applications through site-to-site VPN or whitelisting the on Demand’s official data centre IP addresses
Comprehensive Dynamic Application Security Assessment Approach
WebInspect
Our DAST technologies support web applications, web services, and mobile-browser optimized applications. What makes Fortify on Demand DAST assessments unique is that they integrate three essential components: Fortify WebInspect by OpenText automated testing, manual analysis, and optional active IAST.
- Best-in-class Dynamic Application Security Testing
- Extensive coverage across 250+ vulnerability categories
- Flexible authentication for improved session management

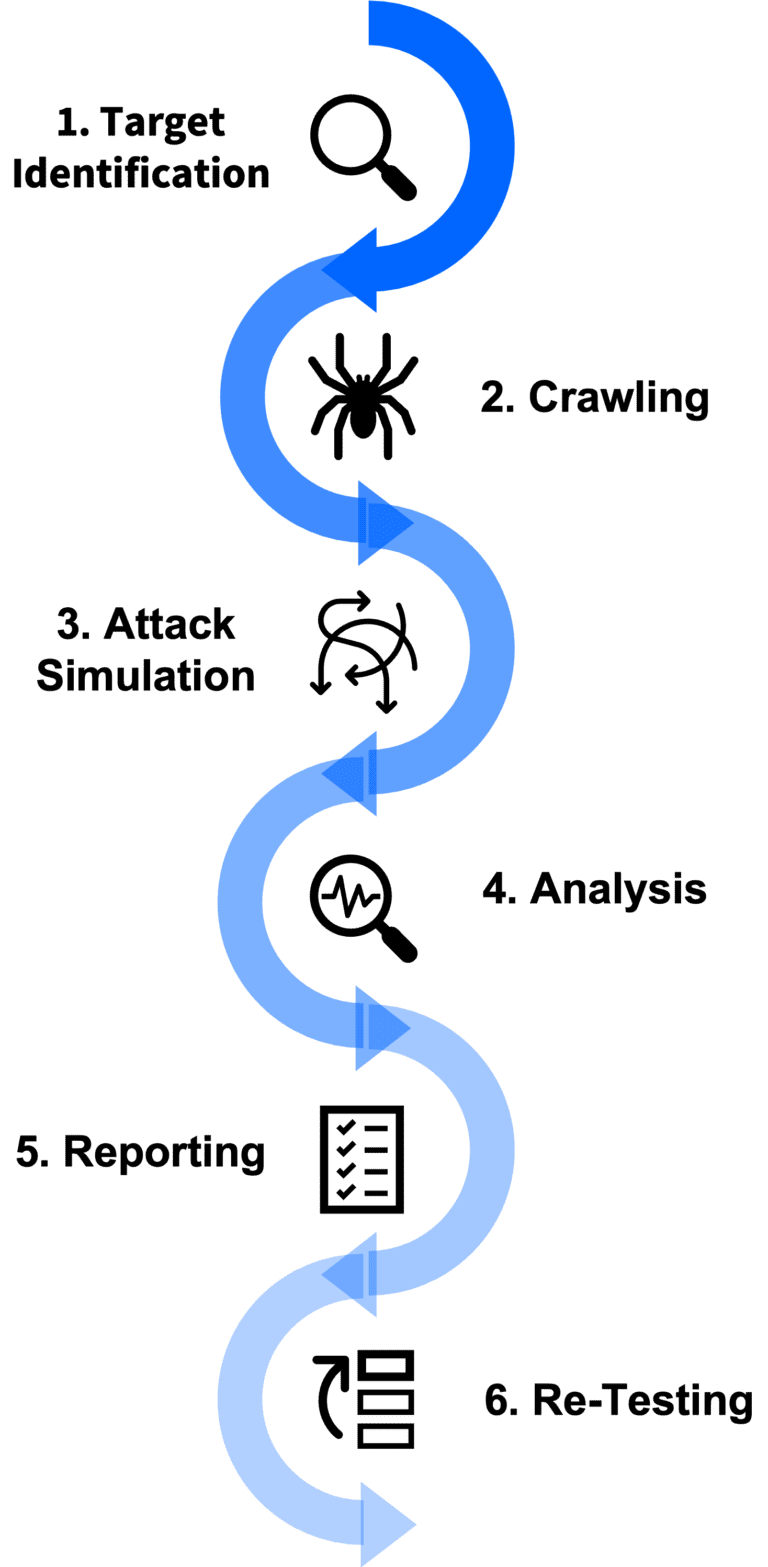
Manual Analysis
Fortify on Demand works as an extension of your in-house application security team. We recognize the significant time and money your team has spent in developing new applications. Your business may not have the time nor the in-house expertise to review extensive reports to validate scan coverage and remove false positives. Fortify on Demand, in its commitment to ensure actionable results, takes the extra step to manually review all initial dynamic scan results with its dedicated team of 150+ global security experts. This includes the isolation and the removal of false positives. Some of the tasks performed by the Fortify on Demand testing team include:
- Proven to remove 99% of false positives
- Results reviewed by 150+ global security experts
- Supports automated scanning with advanced, targeted penetration testing
Our team can also manually analyze the target web application or web service for up to 8 hours using Fortify on Demand’s testing methodology to augment the WebInspect scan results with advanced, targeted penetration testing. Our experts conduct an in-depth examination of the application’s authentication scheme, session management, access control, and a review for logical flaws and faulty developer assumptions. They identify vulnerabilities that can only be detected through human intervention, including, but not limited to:
- The ability to harvest user accounts
- Bypassing multi-step authentication
- Password reset flaws
- Accessing other users’ data or sensitive content
- Horizontal or vertical privilege escalation
- Skip key transaction steps such as shopping cart payments
- Abuse of discount or business limit restrictions
- Unique business logic flaws due to faulty developer assumptions
Active IAST
On-demand customers have the option of integrating active IAST (Interactive Application Security Testing) Agent during the dynamic assessment process. The IAST Agent is installed on the application runtime server and automatically synchronizes with WebInspect during our on Demand dynamic assessment. Benefits of the IAST Agent include:
- Improved coverage (All major components of the attack surface are tested)
- Greater accuracy (Fewer false positives are generated)
- Faster remediation (Full stack trace provided for each issue identified)
SAST
Static
DAST
Dynamic
IAST
Interactive
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.


