Managed Security Service
CONTINUOUS THREAT EXPOSURE MANAGEMENT
Gain a clear overview of your internal and external security posture with clear ratings and indexes for various risk factors.
Pivot to cyber risk management from traditional vulnerability management

Continuous threat exposure management
stay on top of your entire threat exposure with continuous threat exposure management
"The exposure to a range of new cyberthreats is a growing issue for organizations. Security and risk management leaders should use this Strategic Roadmap to pivot from traditional technology vulnerability management to a broader, more dynamic continuous threat and exposure management practice. Gartner's 2024 Strategic Roadmap for Managing Threat Exposure
GARTNER

Benefits of Satius Security's CTEM as a Service
Satius Security offers CTEM as a managed service. Therefore, providing a framework for ongoing assessments, guidance, and reporting to enhance your overall risk management and cyber resilience.
Holistic
The foundation of our CTEM as a service is having a holistic and structured coverage of risk including: Internal, External, Cloud and Compliance Correlation.
Real-Time
Unlike ad-hoc assessments performed at different points in time, our continuous assessments and validations provides a real-time insight into the overall security posture.
Clear
Clear and defensible data is at the core of our service. Presenting a clear insight into all risks and a road map to improve and maintain cyber resilience.
Reporting
Get the answers Executives need to provide directions with actionable insight reporting and defensible data to drive improvement and resiliency.
Exper-Led
The program is managed by certified expert cybersecurity engineers with the knowledge and expertise in all phases of the CTEM program.
Managed
Meet tight budgets and shortage of resources with Satius Security's to managed the program and provide desired results.
Executive Management need Holistic strategy to cyber risk
Companies are rolling out a wide range of activities to counter cyber risk. They are investing in capability building, new roles, external advisers, and control systems. What they lack, however, is an effective, integrated approach to cyber risk management and reporting

A holistic approach proceeds from an accurate overview of the risk landscape—a governing principle that first of all requires accurate risk reporting. The goal is to empower organizations to focus their defenses on the most likely and most threatening cyber risk scenarios, achieving a balance between effective resilience and efficient operations. Tight controls are applied only to the most crucial assets. The holistic approach lays out a path to root-cause mitigation in four phases
Cyber risk is now as important a priority for the leaders of public and private institutions as financial and legal risks. Facing a rising threat level and the magnitude of the potential impact, executives are insisting on full transparency around cyber risk and effective ways to manage it actively. They expect reporting to be:
Cyber Risk reporting that produces actionable insight
Companies are rolling out a wide range of activities to counter cyber risk. They are investing in capability building, new roles, external advisers, and control systems. What they lack, however, is an effective, integrated approach to cyber risk management and reporting
Boards and committees are swamped with reports, including dozens of key performance indicators and key risk indicators (KRIs). Reports are often poorly structured, with inconsistent and usually too high levels of detail.
Executive management level reporting should include strategic metrics, operational metrics, cyber economic, and benchmark data presented in clear, structured, and in real-time. only then, management can have effective and meaningful involvement in cyber security strategy and ensure effective governance.
Most reporting fails to convey the implications of risk levels for business processes. Board members find these reports off putting— poorly written and overloaded with acronyms and technical shorthand.
Different groups in the same organization often use different, potentially conflicting information to describe or evaluate the same aspects of cyber risk. To compound the problem of conflicting reporting, underlying data are often too dated to be of use in managing quickly evolving cyberthreats.
An active and holistic approach to cybersecurity begins with an accurate overview of the internal and external risk landscape. This onside-to-inside view helps define the cybersecurity’s implications for governance, organizational structures, and processes. Top executives need a comprehensive and integrated approach to support rapid, fact-based cyber risk management.
Our Approach to Continuous Threat Exposure Management
structured & holistic
Comprehensive visibility and measurement
- External Attack Surface
- Internal Security Posture
- Cloud Security Posture
- 3rd Party Risk Intelligence
clear
Clear picture of risk presented in an understood format, begins with consistent and reliable data sources.
Our continuous assessments cover all threat exposures and present them in aggregated reports and dashboards containing quantification of risk, letter grades, and useful high-level metrics.
- Attack Surface Identification
- Cloud Security Posture Management
- Security Controls Validation
- Attack Path Analysis
- Detection Rule Validation
- Reporting
real time
The security outcomes needed to rapidly respond
Continuous assessments and monitoring to provide real-time reporting and alerts.
Continuously assess readiness for your biggest threats such as: ransomware susceptibility externally, or actual internal readiness.
Drive collaboration and mobilization to take corrective measures.
CTEM Vs. Vulnerability Management
Shift to Holistic Risk Management
CTEM offers a practical alternative to traditional risk-based vulnerability management (RBVM) and prevention-focused methods. By implementing a CTEM program, organizations can continually assess digital asset accessibility and vulnerability, prioritizing remediation based on established risk acceptance and operational viability. At Satius Security, we align with CTEM by using advanced tools to analyze an organization’s attack surface, simulate various scenarios, and validate security controls through controlled attack simulations. By operationalizing CTEM, organizations can proactively identify and mitigate cyber threats, enhancing overall resilience.
WHY SATIUS?
Your trusted partner for Managed Services
- Expertise in security challenges
- Rated 9/10 for overall customer satisfaction
- Accredited engineers in offensive security
- An outcome-focused approach
- Red and blue team security expertise
- Technology agnostic
Why adopting Continuous Threat Exposure Management CTEM?
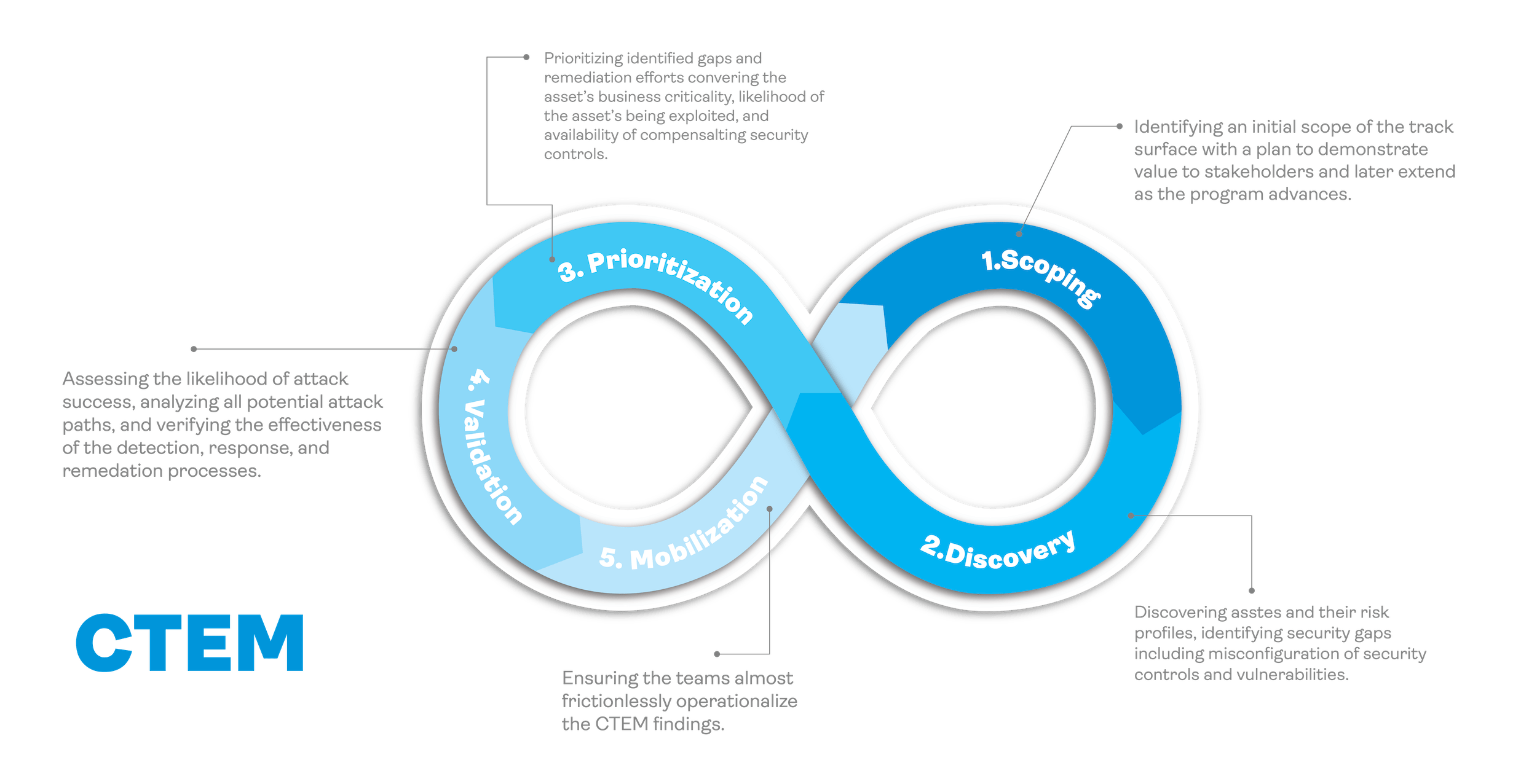
CTEM as a Service provides a comprehensive five-step process to identify and mitigate threats to an organization’s networks and systems. This service enables organizations to evaluate their security posture and detect vulnerabilities.
Unlike vendor-specific technologies or tools, CTEM offers a structured approach that empowers organizations to prioritize potential threats and corresponding remediation efforts effectively, especially in the context of an expanding attack surface.
By adopting the CTEM program, organizations can proactively manage their security risks, keeping pace with evolving threats. The CTEM approach transcends traditional, reactive vulnerability management, offering a practical and proactive strategy to address and mitigate the most critical risks.
- Proactive Risk Management: CTEM continuously monitors digital infrastructure, addressing vulnerabilities before they escalate.
- Prioritization of Threats: Assessing impact and allocating resources efficiently.
- Enhanced Cyber Resilience: Iteratively refining defenses for continuous improvement.
- Actionable Insights: Generating real-time threat data for effective remediation.
- Alignment with Business Objectives: Integrating strategic goals into cybersecurity strategies.Adaptability: Evolving alongside technological advancements and emerging threats.
In comparison to traditional vulnerability management, CTEM is proactive, holistic, aligned with business goals, promotes continuous improvement, integrates with existing security controls, and emphasizes validation through simulation tools.
CTEM stands apart from traditional vulnerability management programs in several key ways:
- Proactive vs. Reactive Approach: Traditional programs reactively address vulnerabilities post-discovery, while CTEM proactively monitors the threat landscape, prioritizing preemptive remediation to mitigate potential exploits.
- Broader Scope: While traditional programs often focus solely on technical vulnerabilities, CTEM takes a holistic view, recognizing threats from various sources such as configuration errors, credential misuse, and insider risks.
- Business-Aligned Prioritization: Traditional approaches may struggle to prioritize remediation efforts effectively, whereas CTEM aligns priorities with business objectives, concentrating on threats that pose the greatest risk to critical assets.
- Continuous Improvement: Traditional methods tend to be static, with periodic scans. In contrast, CTEM emphasizes continuous enhancement by perpetually monitoring.
- Integration with Security Controls: While traditional practices often operate independently, CTEM integrates seamlessly with existing security measures, promoting a cohesive strategy for managing threat exposure.
- Emphasis on Validation: Traditional approaches rely on theoretical assessments, whereas CTEM places a premium on validation. It employs tools like Breach and Attack Simulation (BAS) and Security Control Validation to simulate attacks and verify the effectiveness of defensive measures.
Businesses of all sizes and across various industries can apply Continuous Threat Exposure Management (CTEM). The concepts of CTEM can benefit any organization, regardless of its size or industry. These concepts include being vigilant for potential threats, prioritizing what is essential for the business, and continuously striving for improvement. By implementing these ideas, organizations can enhance their overall performance and success.
All organizations, regardless of size, can benefit from using a CTEM program. This includes small businesses just beginning to use digital tools and large companies with multiple digital systems. A CTEM program can help businesses in various ways. CTEM is flexible and scalable, making it easy to adapt to the specific needs and resources of any organization.
CTEM is important for industries that deal with sensitive data such as finance, healthcare, IT, and e-commerce. Industries facing cybersecurity threats should adopt a proactive and constantly improving approach to address them.
The same holds true for businesses operating in regulated industries. CTEM not only enhances security measures but also ensures compliance with industry-specific cybersecurity regulations.
Scoping within the Continuous Threat Exposure Management (CTEM) cycle entails a meticulous examination of the infrastructure segments to be encompassed in the process. It necessitates a thorough comprehension of the organization’s business aspects to establish an appropriate scope for the CTEM initiative. For a pilot CTEM program, an ideal scope might involve scrutinizing the external attack surface and the security posture of Software as a Service (SaaS) systems.
The process initiates with an exhaustive discovery phase, which entails assessing the entire attack surface—externally, internally, and within the cloud. As the CTEM cycle advances, refining the scope becomes imperative. This stage underscores the importance of precise metrics, which should encompass network segment specifics, security control data, identified threat categories, threat tactics and techniques, quantified risk factors, and overall cyber resilience metrics. These metrics, originating from the initial scoping phase, serve as a basis for aligning the refined scope with the organization’s strategic cybersecurity objectives.
Ready for Cyber Resilience?
Learn more how our Managed Service can help you achieve Cyber Resilience and be an extension of your team without breaking the budget.

TESTIMONIALS
What our clients say about us

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial
Latest news
Satius Security has a comprehensive grasp of the obstacles both small to medium-sized businesses (SMBs) and enterprises encounter in achieving compliance with security frameworks and maintaining an ideal security stance.