Elevate Your Security Posture with Continuous Threat Exposure Management (CTEM)
Proactively Identify, Validate, and Remediate Threats Across Your Attack Surface with Our Managed CTEM Service.
Our Managed CTEM Service Provides Continuous Assessment and Improvement of Your Security Posture, Offering Real-Time Insights and Actionable Reporting to Bridge the Gap Between Executive Management and IT Teams.

KNOW YOUR RISK LEVEL

Cyber Risk in Financial Terms.
QUICKLY CLOSE GAPS

Validate Effectiveness of Prevention Controls.
FOCUS ON CRITICAL EXPOSURES NOT VULNERABILITIES

Quickly Respond to New Exposures, Not Vulnerabilities for More Efficient Risk Management.
Let us resolve your security challenges
We understand the unique challenges of cybersecurity and the changing attack landscape. Our staff are innovative, highly flexible, and focused on the client.
Seamlessly Operationalize Continuous Threat Exposure Management (CTEM)
Achieve CTEM without the complexity of managing additional tools. Tailor the scope and frequency of assessments to align with your unique threat vectors, security stack, and budget.
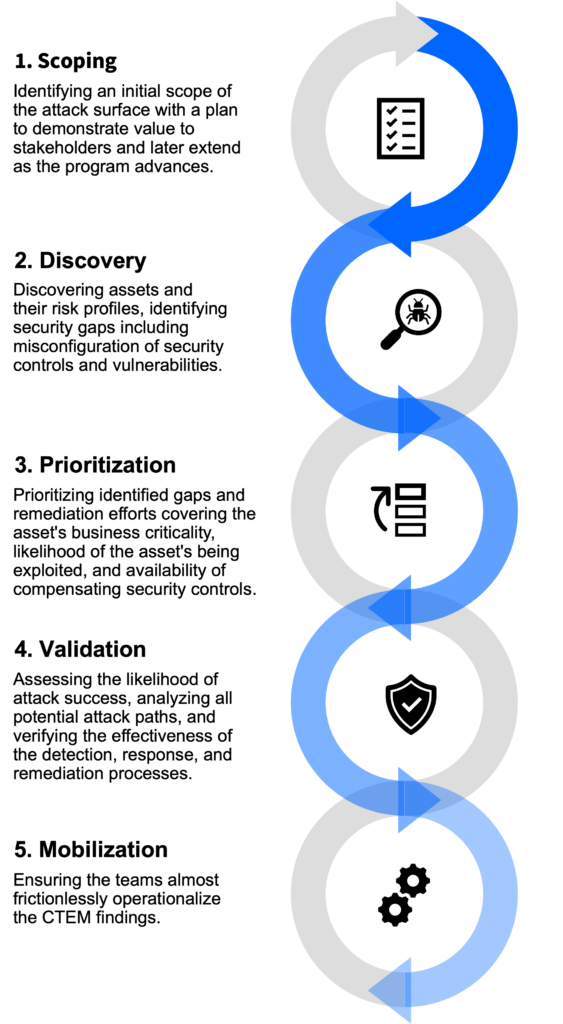
Continuous threat exposure management
stay on top of your entire threat exposure with continuous threat exposure management
"The exposure to a range of new cyberthreats is a growing issue for organizations. Security and risk management leaders should use this Strategic Roadmap to pivot from traditional technology vulnerability management to a broader, more dynamic continuous threat and exposure management practice. Gartner's 2024 Strategic Roadmap for Managing Threat Exposure
GARTNER
Ransomware Resilience as a Service
Shift to Ransomware Resiliency
Organizations of all sizes and across industries continue to be challenged with managing the risk and impacts of ransomware attacks. Developing a methodical approach to strategize, plan, prevent, detect, respond, recover, and report ransomware attacks is critical to effectively mitigate the inherent risks and impacts posed by ransomware. One of the greatest challenges ransomware attacks present is the wide range of possible attackers because the attacker can be anyone using any of the many different attack vectors.

Expert Led Assessments to enhance your cyber resilience & Meet Compliance
Satius Security understands the challenges facing organizations including latest threats. Discover our range of On-Demand and Managed Services to reduce risks and enhance your organization’s cyber resilience.
OUR APPROACH
Why Can You Rely on Satius Security for Cyber Resilience?

Premium cybersecurity services designed to safeguard your organization against advanced threats.
Our high-quality solutions encompass a comprehensive range of security measures including risk assessment, adversary simulations, detection, and response capabilities. Leveraging cutting-edge technology and expert knowledge, Satius Security ensures robust protection of your digital assets, continuity of operations, and compliance with industry standards.

The latest cyber offensive intelligence to identify and address security risks
Defending against cyber threats requires an in-depth understanding of how attackers operate. Our extensive experience of conducting pen testing, breach & attack simulations, red teaming and other engagements for diverse environments means we have first-hand knowledge of the latest adversarial tactics and wide-ranging insight into how to safeguard against them.

We meet our clients’ security needs with guidance that’s actionable and effective
You should rely on our specialists to reduce the burden of security management and deliver the outcomes you need. By working closely with your team and applying our extensive experience across a range of industries we better understand the challenges facing your organization.

We select the best tools that align with your needs without being limited to certain vendors.
At Satius Security, we select the best tools for each of our clients based on their requirements and budget. Some managed security service providers are inflexible in their approach to the technologies they use.
CISOs: Elevate Your Cybersecurity Reporting to the Boardroom
Struggling to bridge the gap between technical cybersecurity metrics and what your board actually wants to see? You’re not alone.
Download our free guide:
“CISO’s Guide To Reporting Cyber Security”
That’s why we’ve created the “CISO’s Guide to Reporting Cyber Security“—a step-by-step resource to help you:
- Present cybersecurity insights in a language the board understands.
- Align security metrics with business goals and priorities.
- Build trust and demonstrate ROI on your cybersecurity investments.
TESTIMONIALS
What our clients say about us

Tedd Long
Partnering with Satius Security has been a game-changer for our organization. Their expert team and proactive approach have provided us with unmatched peace of mind in today's cyber landscape.

Steve Jablonski
Working with Satius Security has been instrumental in bolstering our company's cybersecurity defenses. Their proactive solutions and round-the-clock support have significantly enhanced our resilience against cyber threats. I highly endorse their services to any IT team looking to elevate their security posture.

Elie Hamouche
Satius is a professional IT Security Company that always gives the best value. We benefited from their recommendations and expertise to mitigate findings.

Basheer Altayeb
We have been working with Satius for years to understand and minimize risks. The team performed multiple projects from vulnerability management to security controls validation. very satisfied with the value received.
We work with organisations across a range of industries
- Finance
- Government
- Retail
- Healthcare
- Education
- Industrial

